Setting up RTA Page Types
The standard Run-Time Authentication (RTA) model requires specialized pages:
- Login pageWhen users request pages or resources that require authentication, the
system redirects users to this login page and asks for their username and password. If
successfully authenticated, the system redirects users to the originally requested
page.NoteIf the system uses external SSO (single sign-on) and not Ingeniux CMS as the login gateway, then this URL may be absolute to the SSO website or application.
- Access denied page: If the system cannot authenticate users, the system redirects users to the access denied page, which contains the same login form along with an error message.
- Restricted page index: An index of protected pages that require authentication to access.
RTA pages use specialized schemas, which users can download from the Ingeniux Support Site. Typically, these live in a folder outside the site structure.
The authentication system uses XSL stylesheet templates or MVC Razor views to render authentication controls into user HTML. Every time users log in or out, this group of stylesheet templates creates the HTML forms and links with which users interact.
System administrators can customize the presentation of any authentication control by modifying the template or view that renders it. Changing the template's HTML and CSS can help RTA pages match the look and feel of your site. Content contributors can call templates from anywhere within the pages they create. They can add login and logout controls to the standard page-rendering templates, creating a seamless browsing experience.
This topic provides brief overviews of the following RTA pages and the XSL templates and MVC views that render them:
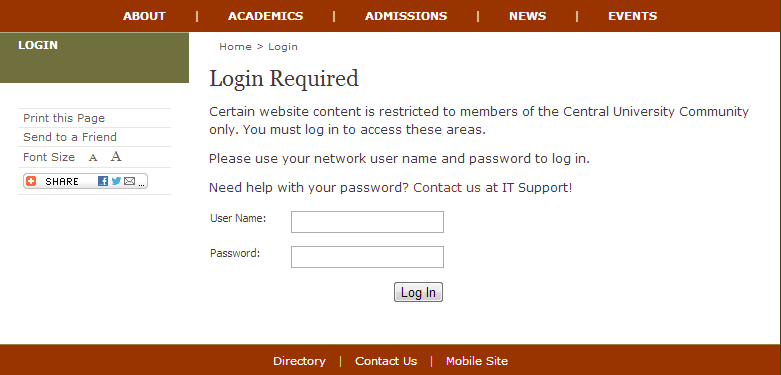
Login Page
Sites that implement RTA without external SSO features must provide a web interface for users to enter their credentials and log in to the system.
XSL
<!-- hidden field for redirection (back) -->
<input name="redir" value="{/*/IGX_Info/GET/redir}" type="hidden"/>The include-rtsession.xsl file contains XSLT templates that define RTA pages. When users attempt to access protected pages, the system calls the IGXRTSESSION_LoginForm XSL template that contains the basic login form. This form submits the entered user name and password data to the handleLogin.xml page.
The login form includes hidden text that indicates a redirection target. The server uses the target to direct authenticated users to the appropriate protected pages.
MVC Razor View
<!-- hidden field for redirection (back) -->
<input name="redir" value="@Request.QueryString["redir"]"="" type="hidden"/>As long as the field names and form submission target are maintained, system administrators can modify the presentation of the login controls. They can change the contents of this template or modify the images and CSS stylesheet that constitute the template's HTML layout.
Any page in the site can call the customized template by including the standard include-rtsession.xsl stylesheet and invoking the IGXRTSESSION_LoginForm template.
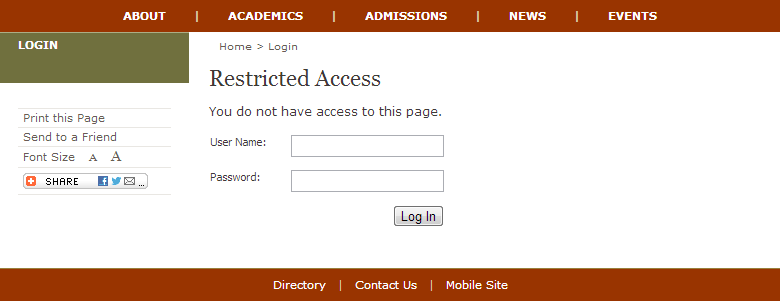
If the system can't validate users' identities, the system redirects users to the access
denied page defined in the @forbiddenFoldersResponsePage attribute of
the Web.config file.
Binary Download Page
When users request files from folders that contain protected assets, the system redirects the user to the binary download page.
XSL
<xsl:template name="IGXRTSESSION_BinaryDownloadDisplay">
<xsl:param name="loginPageUrl">
<xsl:variable name="file" select="normalize-space(/*/IGX_Info/GET/file)">
<xsl:variable name="key" select="normalize-space(/*/IGX_Info/GET/downloadId)">
<xsl:variable name="isMedia" select="normalize-space(/*/IGX_Info/GET/isMedia)">
<xsl:variable name="downloadPath" select="concat($file, '?downloadId=', $key)">
<xsl:choose>
<xsl:when test="$isMedia != 'true'">
<iframe src="{$downloadPath}" _mce_src="{downloadPath}"
style="position:absolute; left: -999px; top: 0px;"
_mce_style="position: absolute; left: -999px; top: 0px;">
</iframe>
</xsl:when>
</xsl:choose>
</xsl:variable>
</xsl:variable>
</xsl:variable>
</xsl:variable>
</xsl:param>
</xsl:template>MVC Razor View
string file = _Functions.GetQuerystring(Model.Page as CMSPageRequest, "file");
string key = _Functions.GetQuerystring(Model.Page as CMSPageRequest, "key");
bool isMedia = _Functions.GetQuerystring(Model.Page as CMSPageRequest, "isMedia").ToBool();
IEnumerable securedDocuments = Model.GetNavigationItems("SecuredDocuments",
NavigationElementType.Navigation, true, true).Where (elt => elt.Schema == "LibraryDocumentComponent");
ICMSLinkElement securedDocument = securedDocuments.Where(elt => elt.GetAttributeValue("DownloadLink").Contains(file)).FirstOrDefault();
if(securedDocument != null)
{
string downloadPath = file + "?downloadId=" + key;
Html.RenderPartial("Editable/Title", new ViewDataDictionary(Model.Element("Title")));
Html.RenderPartial("Editable/BodyCopy", new ViewDataDictionary(Model.Element("BodyCopy")));
if (isMedia)
{
<iframe src="@downloadPath" _mce_src="http://mce_host/xml/@downloadPath" style="position:absolute; left: -999px; top: 0px;"
_mce_style="position: absolute; left: -999px; top: 0px;"</iframe>
<p>
Download will start shortly. If not, please click
<a href="@downloadPath" _mce_href="http://mce_host/xml/@downloadPath">here</a> to start download.
</p>
}
else
{
<p>
Click <a href="@downloadPath" _mce_href="http://mce_host/xml/@downloadPath">here</a> to access media.
</p>
}
}Blocked Access Page
When users attempt to access assets in folders defined as forbidden in Web.config, the system redirects users to the blocked access page.
XSL
<xsl:template name="IGXRTSESSION_BlockAssetDisplay">
<h1>Access Denied by Ingeniux Runtime Authorization System</h1>
<div>
Blocked access to url "<xsl:value-of select="/*/IGX_Info/GET/blockedPath">"</xsl:value-of>
</div>
</xsl:template>MVC Razor View
<h1>Access denied by Ingeniux Run-Time Authentication System.</h1>
<div>Blocked access to URL "@Model.Element("IGX_Info").Element("GET").Element("blockedPath").Value"</div>Logout Link
When logged-in users want to log out, the system uses a second XSL template called IGXRTSESSION_LogoutLink.
XSL
<xsl:template name="IGXRTSESSION_LogoutLink">
<xsl:variable name="noauth">
<xsl:call-template name="IGXRTSESSION_getSessionInfo">
<xsl:with-param name="name" select="'NOAUTH'">
</xsl:with-param>
</xsl:call-template>
</xsl:variable>
<xsl:if test="$rtSessionStr != '' and $noauth != 'TRUE'">
<a href="handleLogout.xml" _mce_href="handleLogout.xml">Log Out</a>
</xsl:if>
</xsl:template>Just like the login XSL template, any location on any page can include this template. However, the page only renders an HTML logout link for logged-in users.
MVC Razor View
string currentUser = page.AuthenticationInformation != null && page.AuthenticationInformation.ContainsKey("Username") ?
page.AuthenticationInformation["Username"] : "";
@if (!string.IsNullOrWhiteSpace(currentUser))
{
<a href="handleLogout.xml" _mce_href="handleLogout.xml">Log Out</a>
}In this example, the retrieval of the NOAUTH variable from the session object prevents the logout link from displaying to logged-out users. Therefore, any page can include this template without confusing users who aren't accessing protected content.
The logout link is nothing more than an anchor tag with an href target of handleLogout, which instructs the server to delete any session information for the user. The anchor deletes the cached session identifier in the database and in the user cookie.
Just like the login form, administrators can change the HTML to customize the presentation of this template. No CSS styles associate with the default logout link implementation, but administrators may use CSS styles to customize presentation.
Next Steps: Define protected pages with RTA to provide security.
